How to configure SSO with Entra ID
This feature requires HTTPS to work.
Since version 3.9, Passbolt Pro Edition supports SSO with Entra ID.
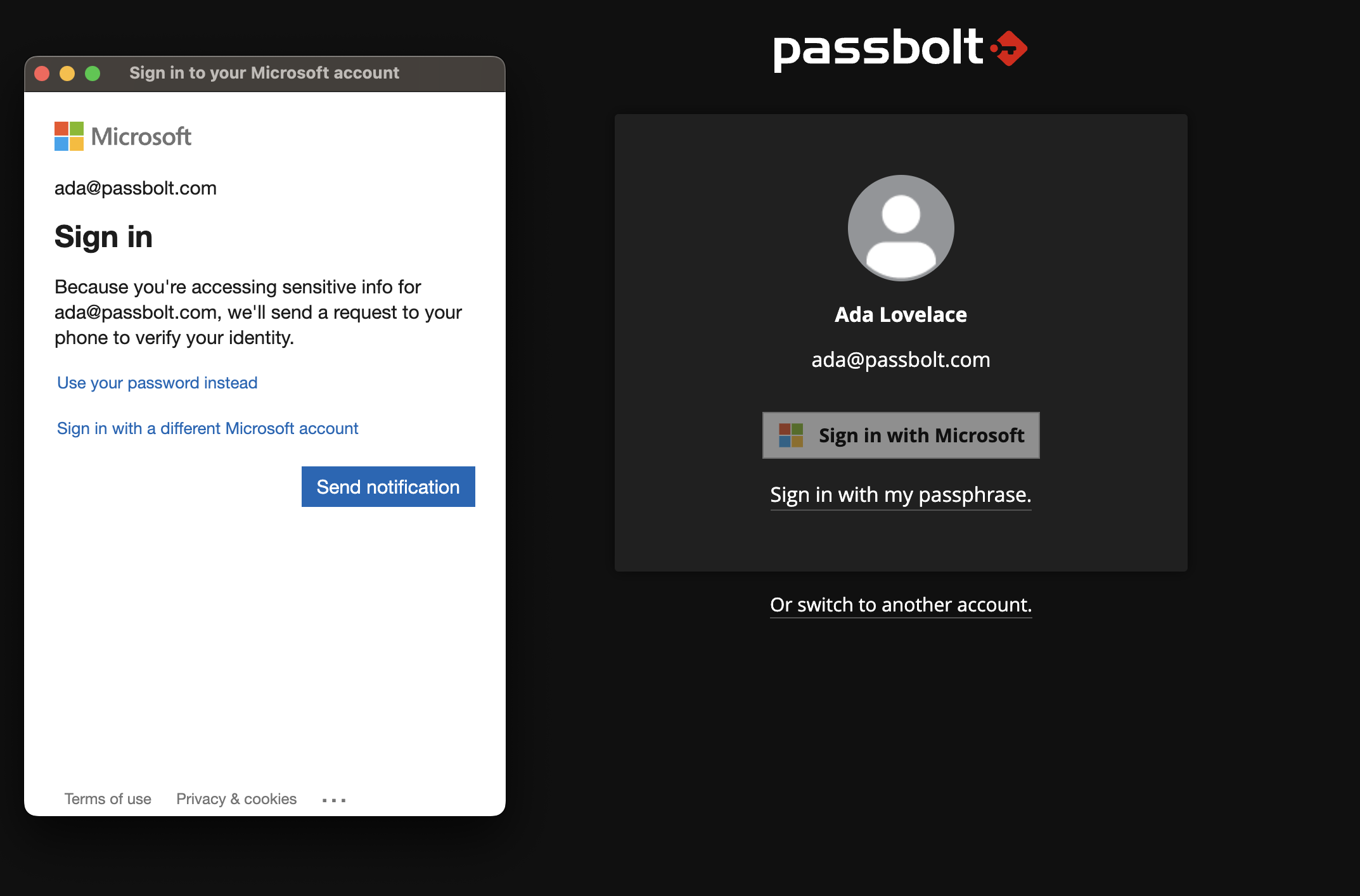
How does it work?
In short Passbolt SSO leverages Entra ID OAuth2/OpenID on top of the existing challenge-based authentication. The user by logging in Microsoft unlocks a key stored server side needed to decrypt the secret key passphrase twice encrypted with a non-extractable symetric key stored in the browser extension local storage client side.
To understand which user flows are supported currently, the risk analysis, and how it works in practice please read the developer documentation.
How to configure the plugin?
Email addresses must match exactly between the SSO provider and Passbolt. Users can only sign in with SSO if their email address exists in both systems.
Open both the Entra admin center and Passbolt:
- You will need to go the administration section of your Passbolt instance and then to the "Single Sign On" section.
- You will need to also login to the Entra Portal.
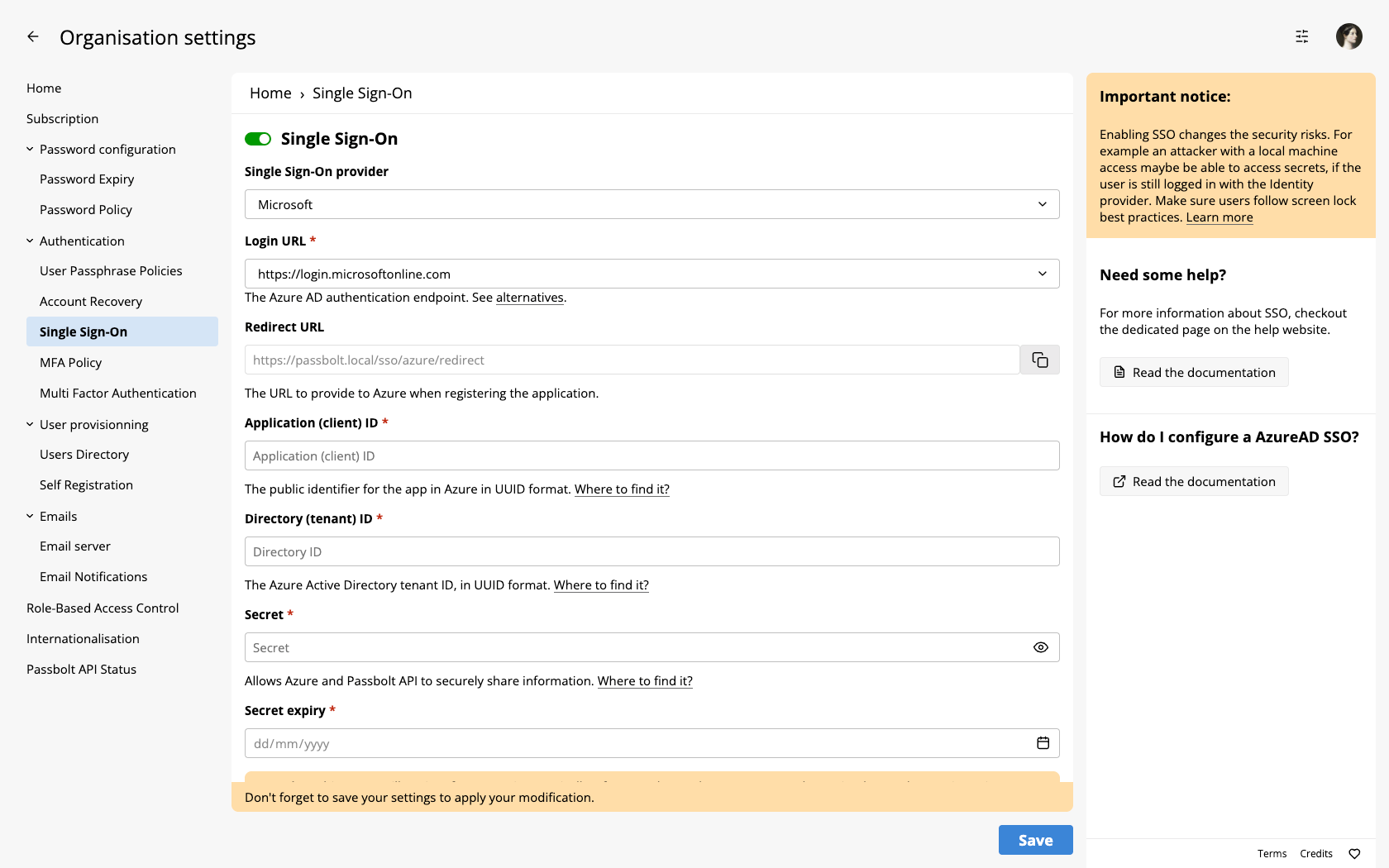
You must ensure users are present both in passbolt and Entra ID, the email is used to correlate accounts.
- Users that are not present in Entra ID but are present in passbolt will not be able to use SSO (a message on microsoft side will be shown).
- Users that are not present in passbolt but are present in Entra ID will not be able to login in passbolt (a message on passbolt side will be shown).
Configure Entra ID
In your Entra ID portal:
- Go to Identity > Overview from the left panel menu.
- Make sure your user email in Azure Directory matches the one in passbolt
- Copy your Tenant ID (a UUID) and paste it in passbolt
- Click on Add > App registration
Register a new application
- Give it a Name such as "Passbolt SSO"
- Select the supported account type you desire. "Accounts in this organizational directory only" is a good default.
- Copy the redirect url from Passbolt to Entra, it should be something like
https://yourdomain.com/sso/azure/redirect. - In "Select a platform", select "Web"
- Click register, you should be back on the Entra application page
- Copy the application (client) ID back to your passbolt instance
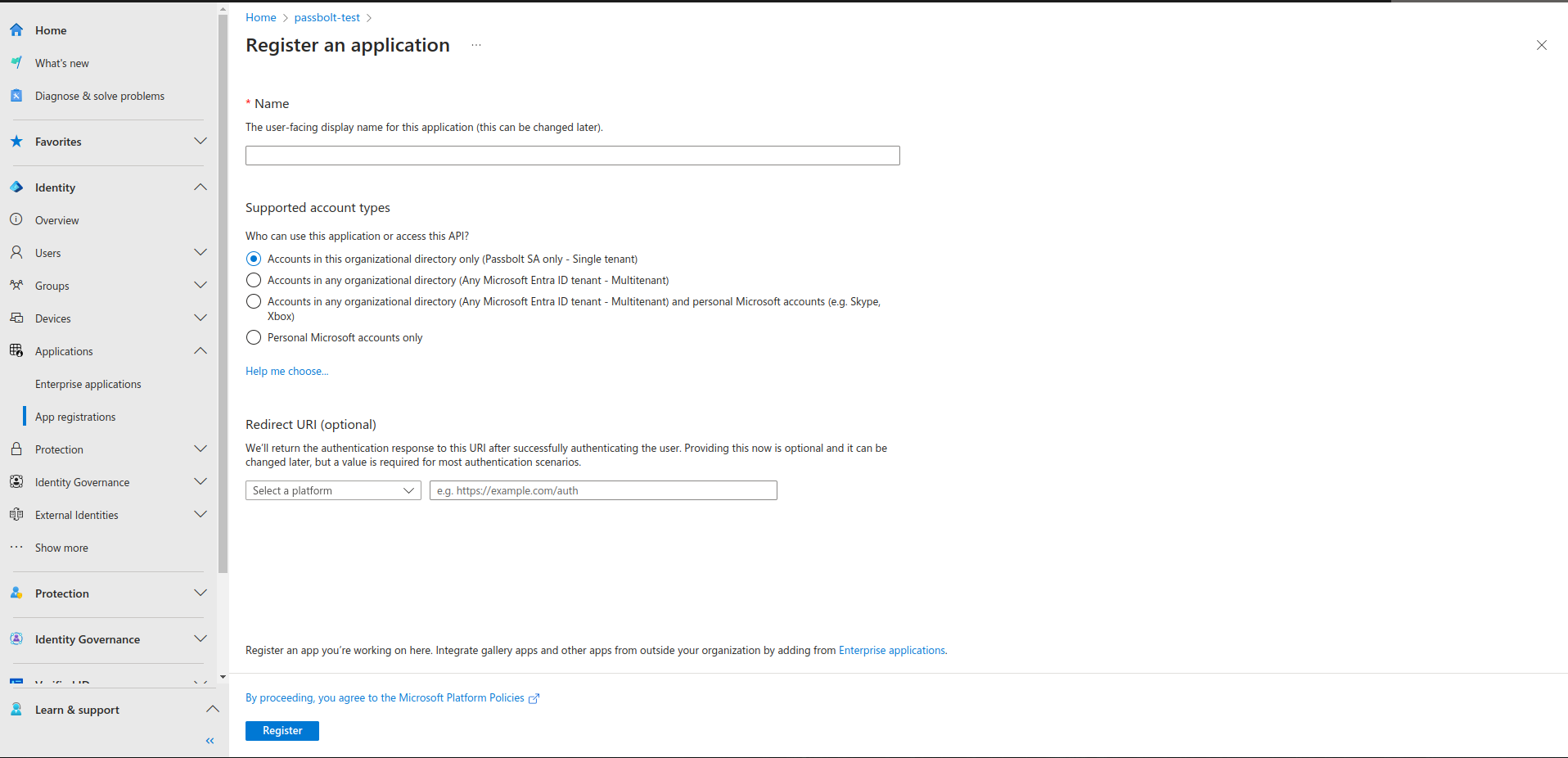
Add a secret for the application
- On the Entra application page, click on "Certificate and secrets"
- Click on "New client secret"
- Choose a name like "Passbolt SSO Secret"
- Select an expiry date
- Copy the secret value and expiry back to your passbolt instance
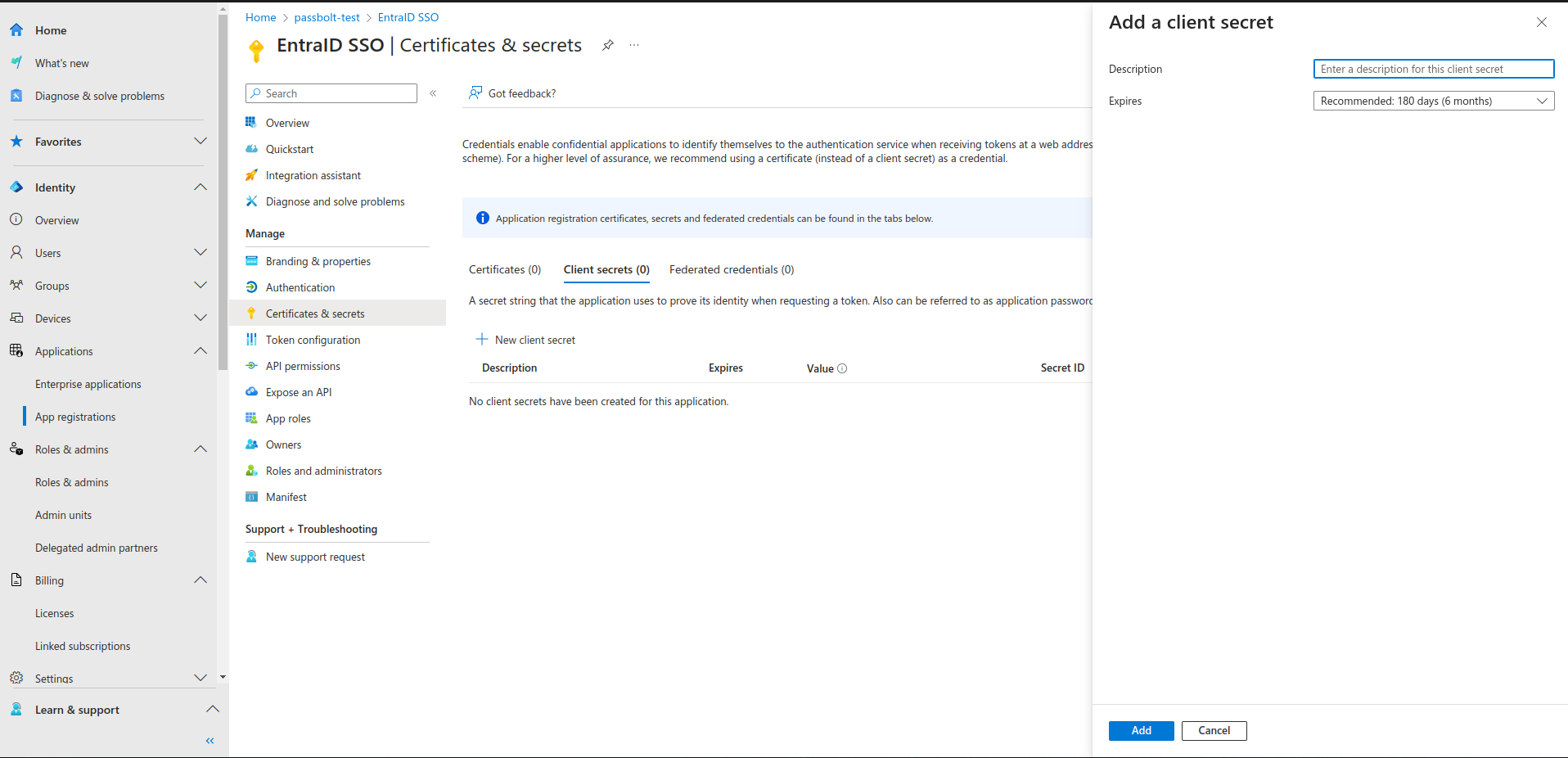
In your passbolt instance:
- Click save settings
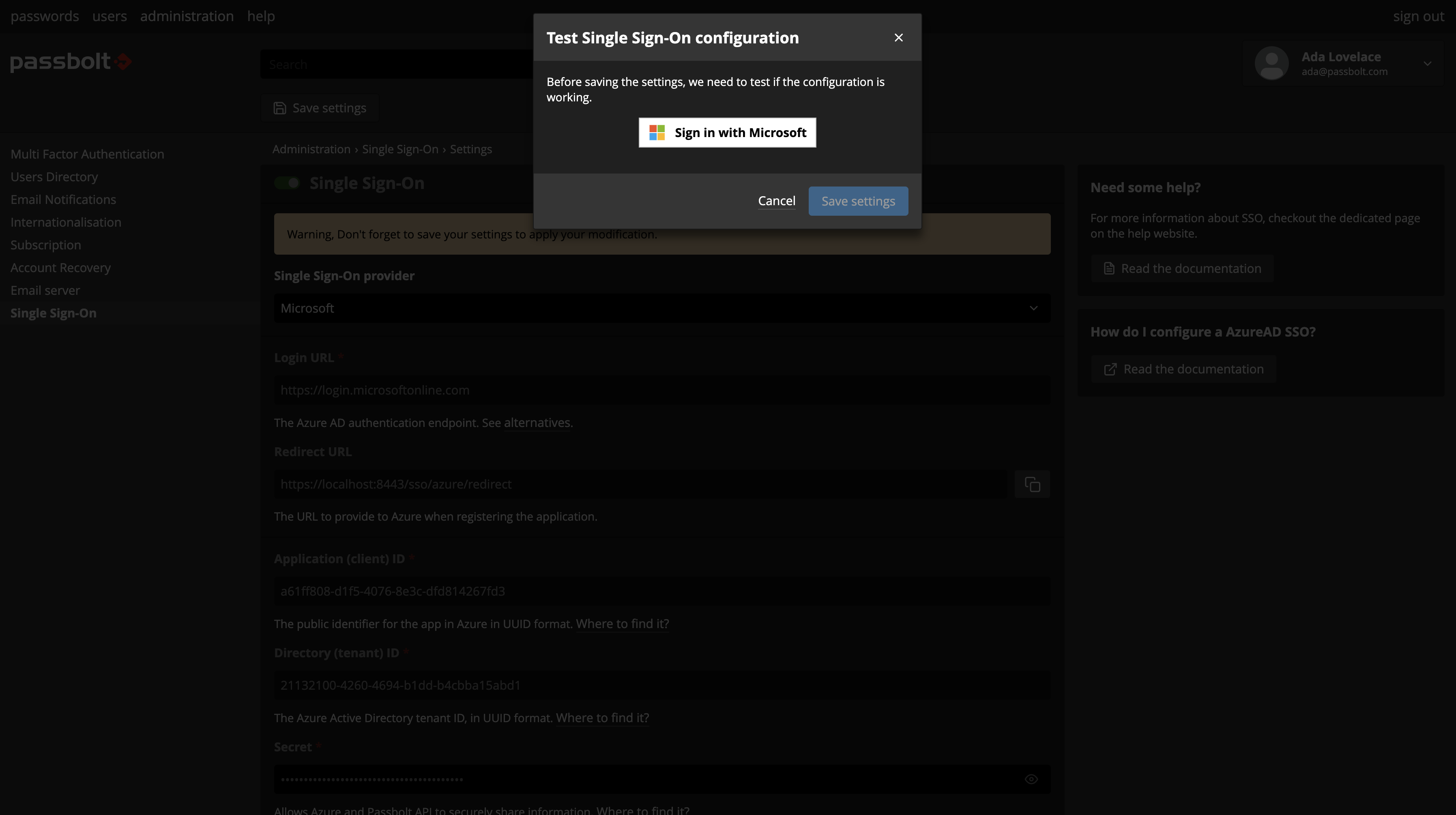
- A dialog will open with Microsoft button, click on it
- A popup will open asking you to perform the authentication with Microsoft
- Once the authentication is successful you can save the settings
- Once the settings have been saved, you can log out, you should then see an SSO option
Please note that users must successfully perform a login using their current passphrase after SSO has been activated in order for the SSO option to be proposed to them at future logins.
Advanced Settings
Email claim
This field will help in order to set which email claim should be used for the authentication, you can chose between:
- UPN (userPrincipalName)
- This will require some extra configuration on azure side as it is an optional claim
- Preferred username
- This is the primary username that represents the user on azure, this could be an email address, phone number or a generic username without a specified format. It is needed to use the
profilescope for this option, you can learn more here.
- This is the primary username that represents the user on azure, this could be an email address, phone number or a generic username without a specified format. It is needed to use the
Prompt
This will help you to configure the authentication method for the users
- Login
- The default prompt method, this is will prompt the user to authenticate with their azure credentials every time they are logging out or being logged out.
- None
- This method will use the active azure session instead and will not ask the azure credentials