Install Passbolt on RockyLinux 9
Prerequisites
For this tutorial, you will need:
- A minimal RockyLinux 9 server.
- A domain / host name pointing to your server, or at least being able to reach your server through a static IP address.
- A working SMTP server for email notifications
- A working NTP service to avoid GPG authentication issues
The recommended server requirements are:
- 2 cores
- 2GB of RAM
FAQ pages:
It is important that you use a vanilla server with no other services or tools already installed on it. The install scripts could potentially damage any existing data on your server.
If you are going to manually provision SSL certificates you may want to do that before beginning!
Package repository setup
For easier installation and update tasks Passbolt provides a package repository that you need to setup before you download Passbolt CE and install it.
Step 1. Download our dependencies installation script:
curl -LO https://download.passbolt.com/ce/installer/passbolt-repo-setup.ce.sh
Step 2. Download our SHA512SUM for the installation script:
curl -LO https://github.com/passbolt/passbolt-dep-scripts/releases/latest/download/passbolt-ce-SHA512SUM.txt
Step 3. Ensure that the script is valid and execute it:
sha512sum -c passbolt-ce-SHA512SUM.txt && sudo bash ./passbolt-repo-setup.ce.sh || echo "Bad checksum. Aborting" && rm -f passbolt-repo-setup.ce.sh
Install passbolt official linux package
sudo dnf install passbolt-ce-server
Importing GPG key 0xC155581D:
Userid : "Passbolt SA package signing key [email protected]"
Fingerprint: 3D1A 0346 C8E1 802F 774A EF21 DE8B 853F C155 581D
From : https://download.passbolt.com/pub.key
MariaDB / Nginx / SSL settings
Passbolt CE RPM package on RockyLinux 9 come with a configuration helper tool to prepare MariaDB, Nginx and SSL settings.
You must prepare beforehand your SSL certificates before launching the tool. Be sure to write down the full path to your cert/key combo, as it will be needed in the nginx configuration process.
Please, notice that for security matters we highly recommend to setup SSL to serve passbolt.
Launch passbolt-configure tool and answer to the questions:
sudo /usr/local/bin/passbolt-configure
MariaDB
If you prefer installing passbolt with Postgres, you can follow our dedicated configuration guide.
================================================================
Do you want to configure a local mariadb server on this machine?
================================================================
1) yes
2) no
#?
Answer 1 for yes if you want to configure a local MariaDB database, otherwise 2 for no if you plan to use an existing one.
If you chose yes, answer the questions:
=======================================================
Please enter a new password for the root database user:
=======================================================
MariaDB Root Password: ****
MariaDB Root Password (verify): ****
======================================================
Please enter a name for the passbolt database username
======================================================
Passbolt database user name:passboltuser
=======================================================
Please enter a new password for the mysql passbolt user
=======================================================
MariaDB passbolt user password: ****
MariaDB passbolt user password (verify): ****
==============================================
Please enter a name for the passbolt database:
==============================================
Passbolt database name:passboltdb
Haveged
On virtualized environments GnuPG happen to find not enough entropy to generate a key. Therefore, Passbolt will not run properly.
You should consider to install Haveged to speed up the entropy generation. Please check our FAQ page about this for more informations.
==================
Install Haveged ?
==================
1) yes
2) no
#?
Nginx
Please enter the domain name under which passbolt will run.
Note this hostname will be used as server_name for nginx and as the domain name to register a SSL certificate with let's encrypt if you don't have your own SSL certificates.
If you don't have a domain name and you do not plan to use let's encrypt please enter the ip address to access this machine.
=========
Hostname: passbolt.domain.tld
=========
SSL configuration
3 available choices for SSL configuration:
- manual: Prompts for the path of user uploaded ssl certificates and set up nginx
- auto: Will issue a free SSL certificate with https://www.letsencrypt.org and set up nginx
- none: Do not setup HTTPS at all
==================
Setting up SSL...
==================
1) manual
2) auto
3) none
#?
If you choose 1, you will be prompted for the full path of your certificates:
Enter the path to the SSL certificate: /path/to/certs/cert.pem
Enter the path to the SSL privkey: /path/to/certs/key.pem
Nginx and MariaDB are now on the way to be configured. You will be notified at the end of the process to connect to the Passbolt web interface to finish the configuration.
===============================================================
Installation is almost complete. Please point your browser to
https://passbolt.domain.tld to complete the process
===============================================================
2. Configure passbolt
Before you can use the application, you need to configure it. Point your browser to the hostname / ip where passbolt can be reached. You will reach a getting started page.
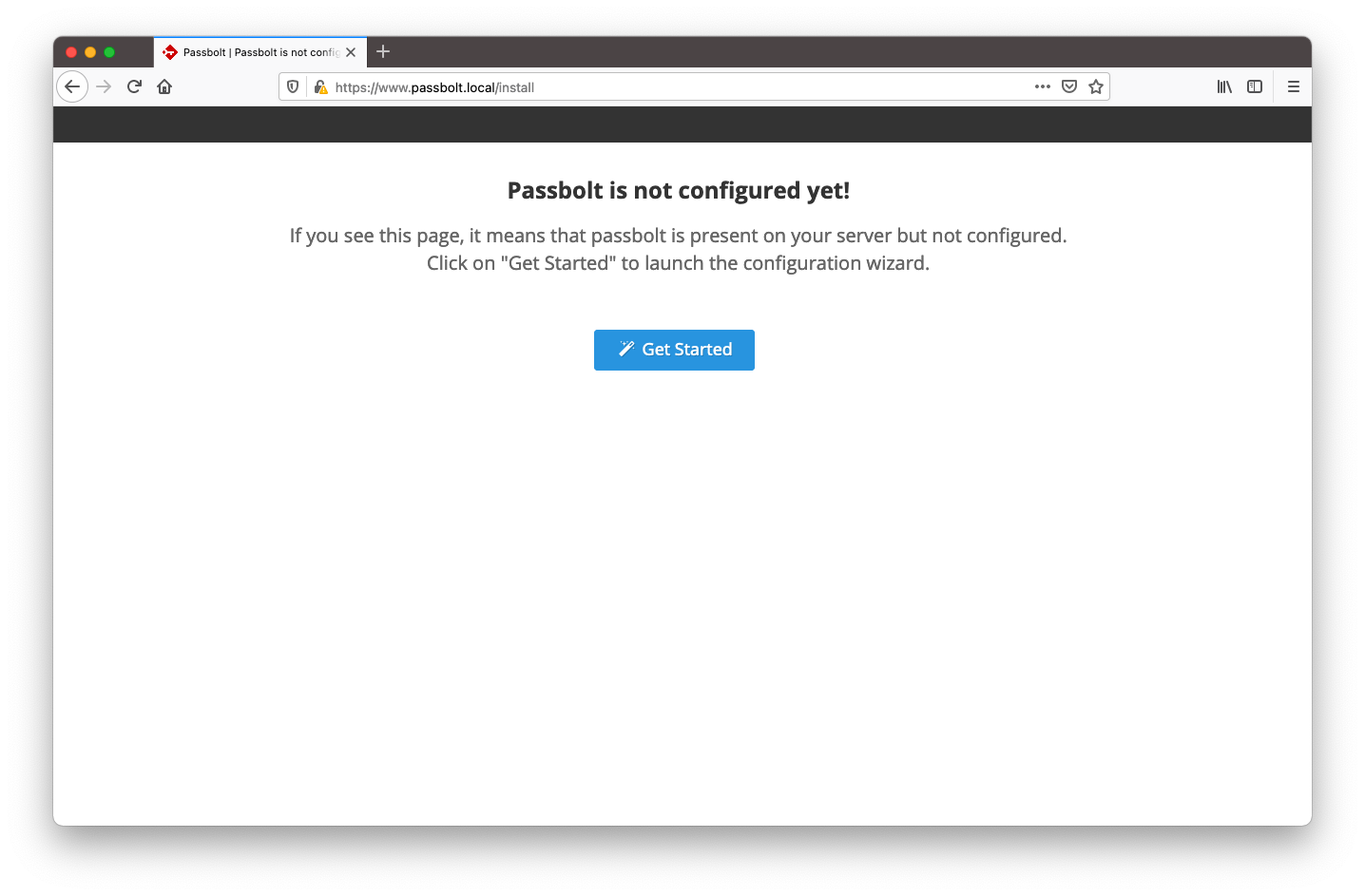
2.1. Healthcheck
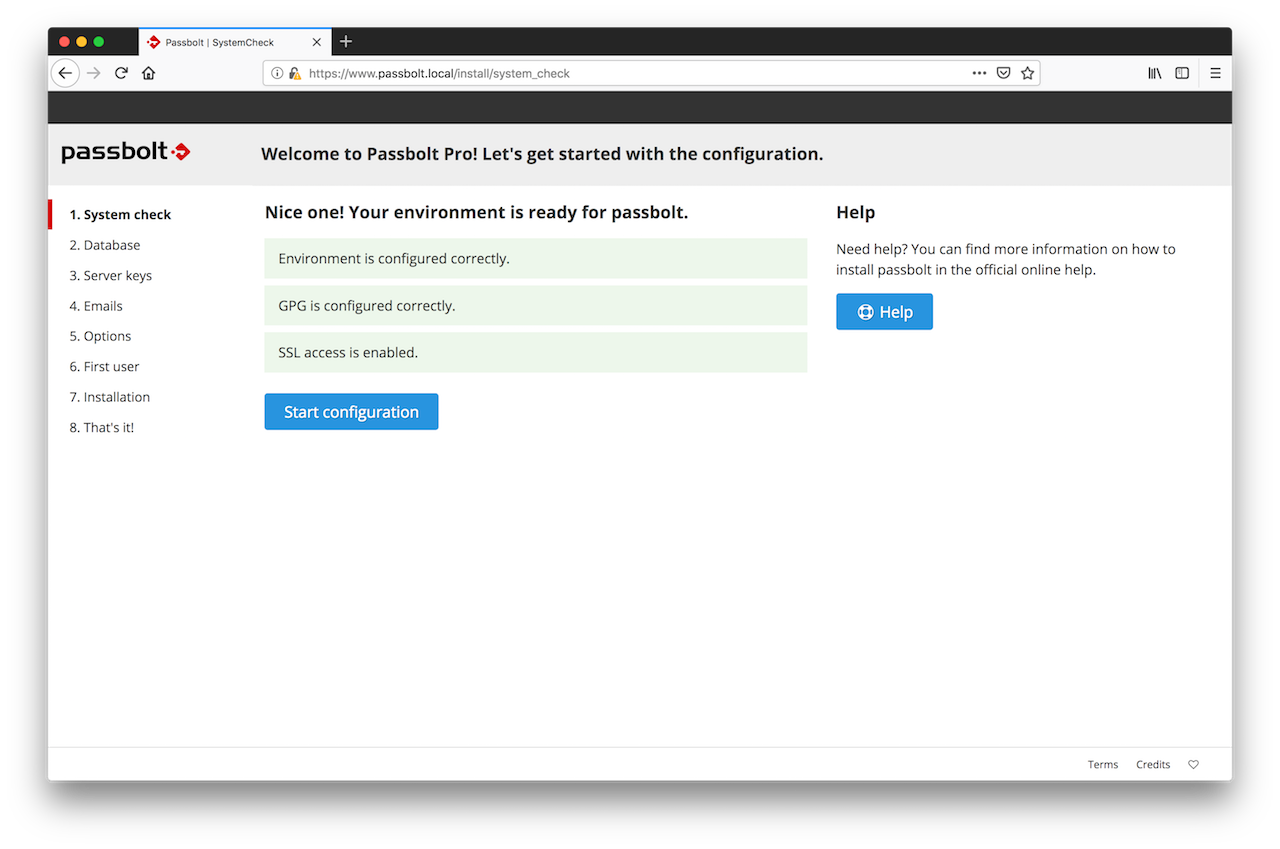
The first page of the wizard will tell you if your environment is ready for passbolt. Solve issues if any and click on "Start configuration" when ready.
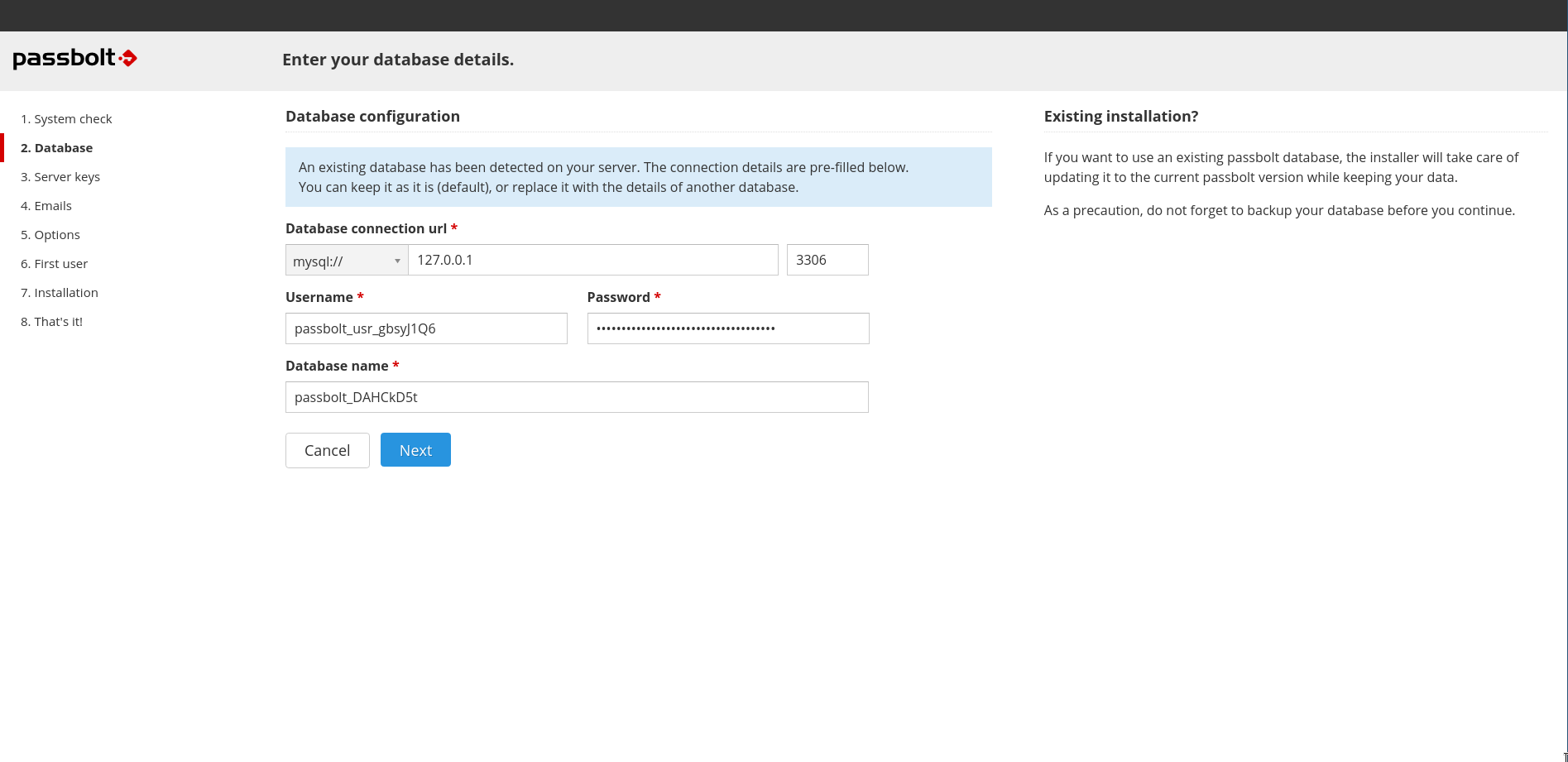
2.2. Database
This step is about telling passbolt which database to use. Enter the host name, port number, database name, username and password.
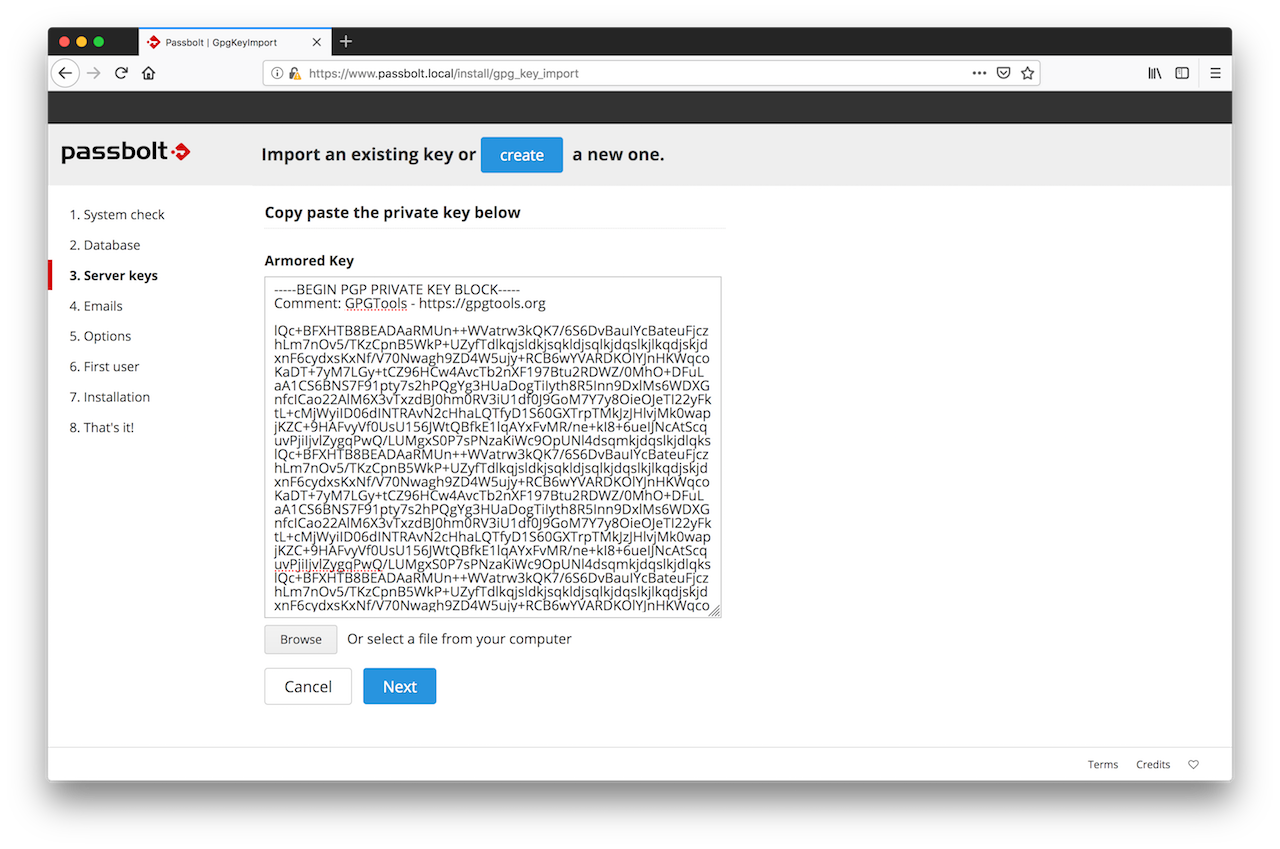
2.3. GPG Key
In this section you can either generate or import a GPG key pair. This key pair will be used by passbolt API to authenticate itself during the login handshake process. Generate a key if you don't have one.
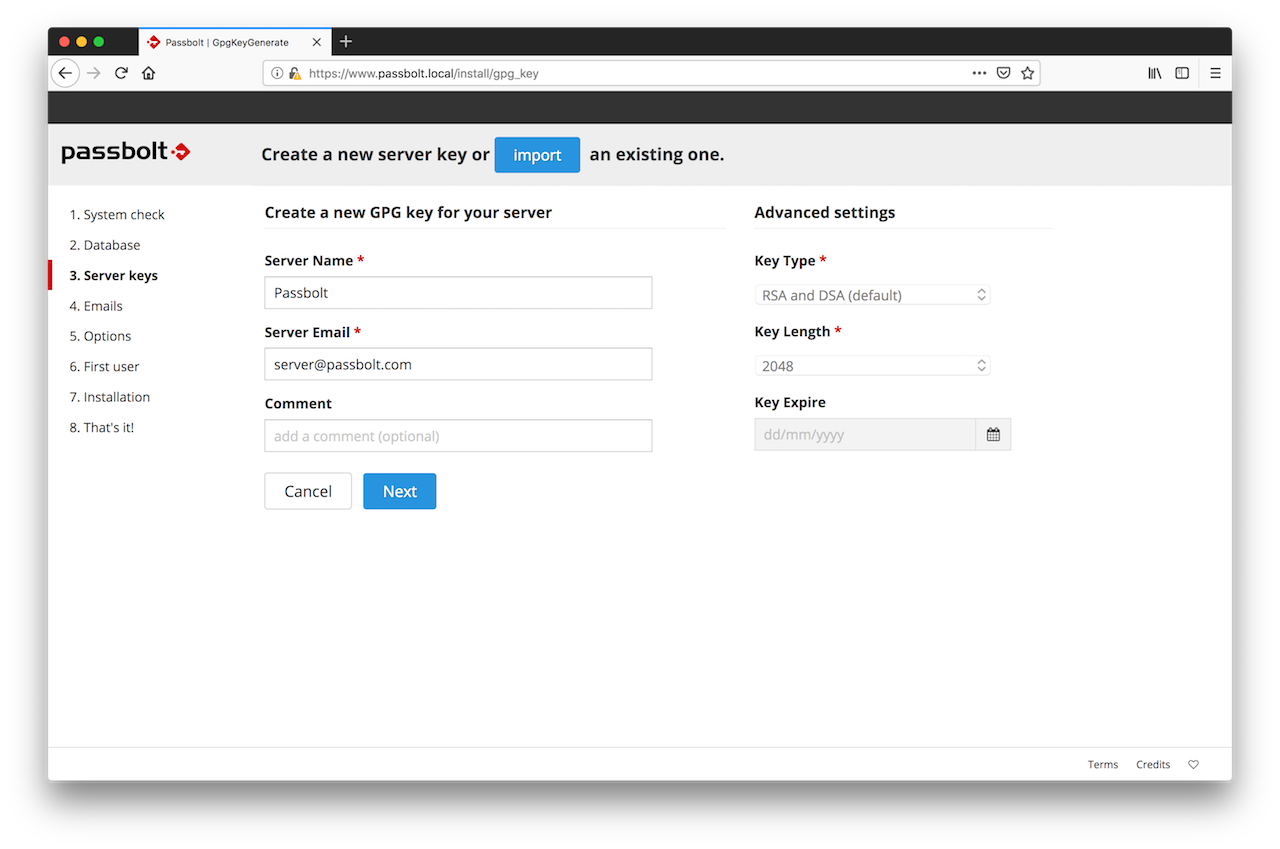
Import a key if you already have one and you want your server to use it.
To create a new GnuPG key without passphrase:
gpg --batch --no-tty --gen-key <<EOF
Key-Type: default
Key-Length: 3072
Subkey-Type: default
Subkey-Length: 3072
Name-Real: John Doe
Name-Email: [email protected]
Expire-Date: 0
%no-protection
%commit
EOF
Feel free to replace Name-Real and Name-Email with your own.
To display your new key:
gpg --armor --export-secret-keys [email protected]
2.4. Mail Server (SMTP)
At this stage, the wizard will ask you to enter the details of your SMTP server.
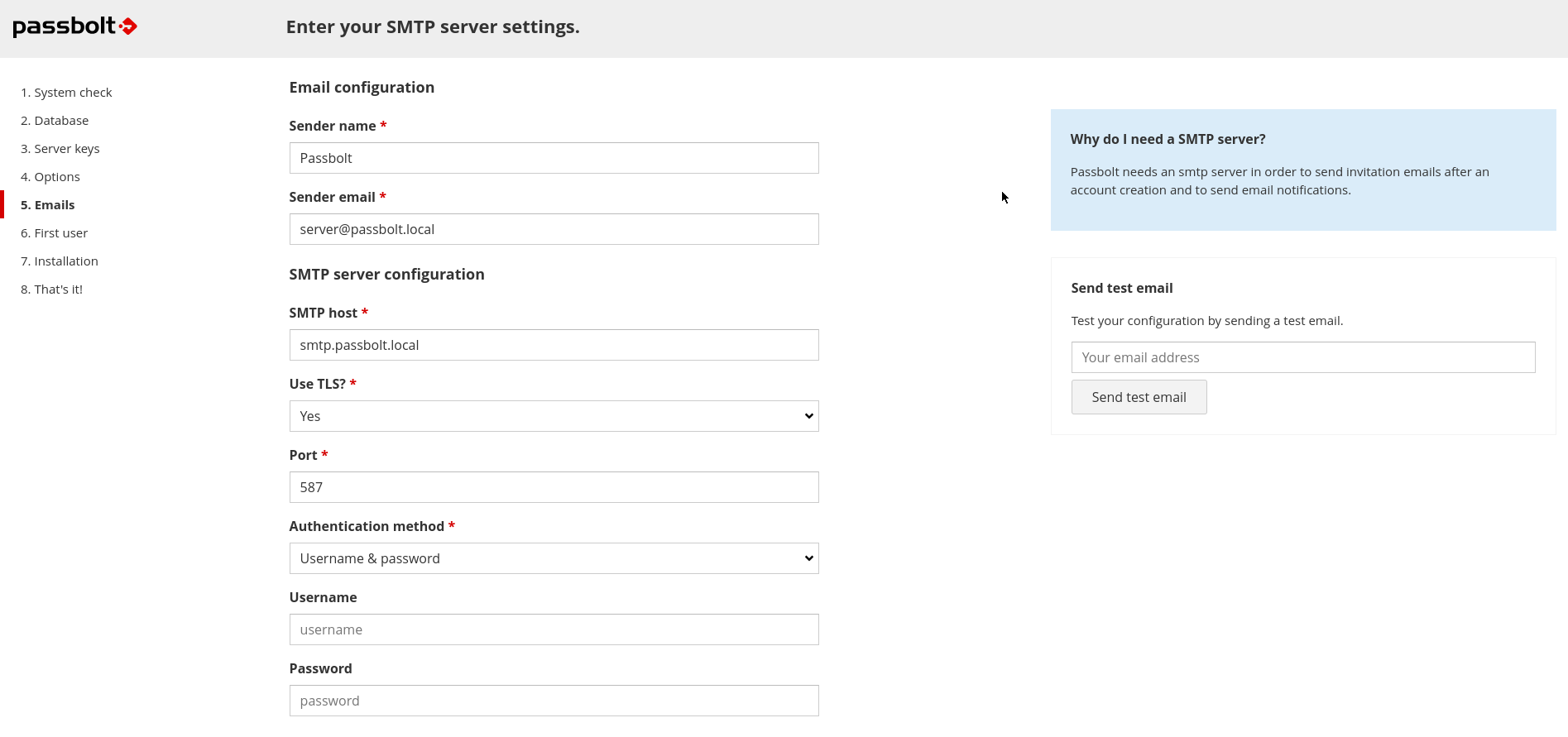
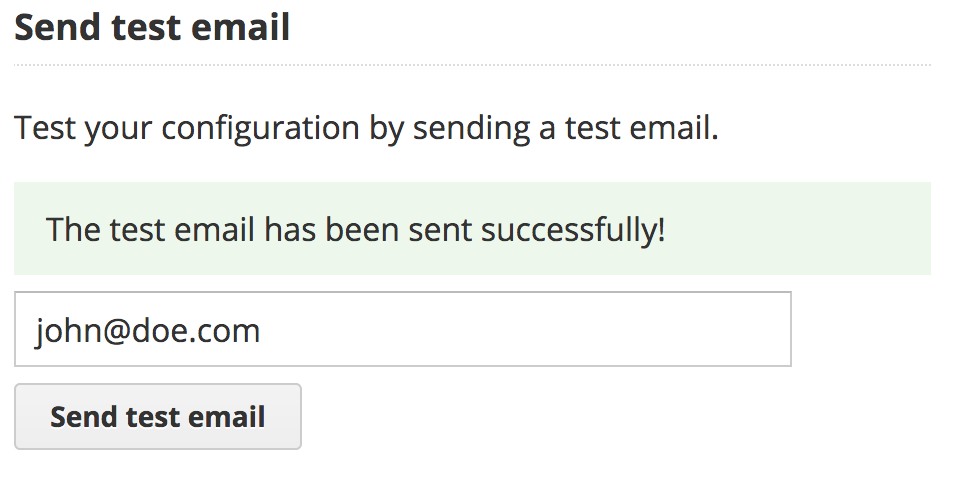
You can also test that your configuration is correct by using the test email feature at the right of your screen. Enter the email address at which you want the wizard to send you a test email and click on "Send test email".
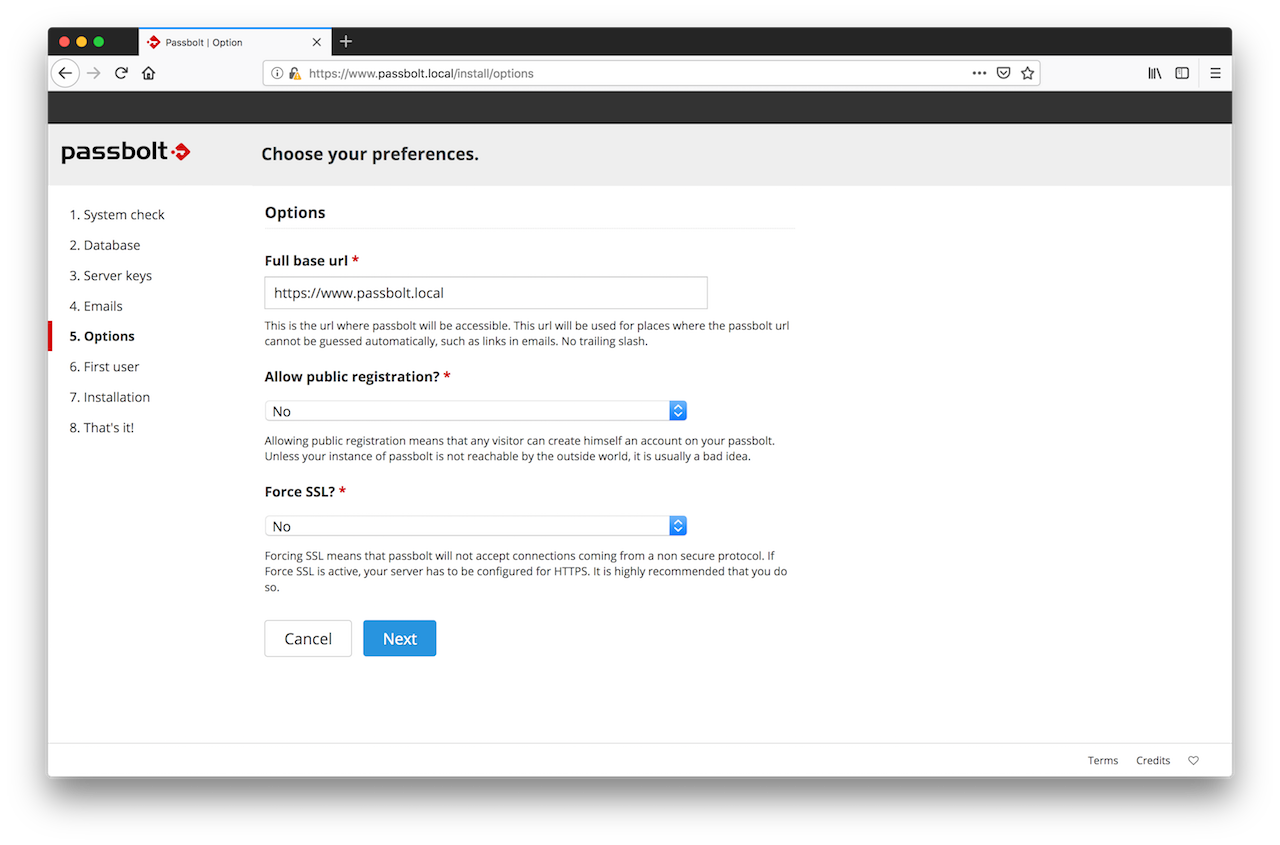
2.5. Preferences
The wizard will then ask you what preferences you prefer for your instance of passbolt. The recommended defaults are already pre-populated but you can also change them if you know what you are doing.
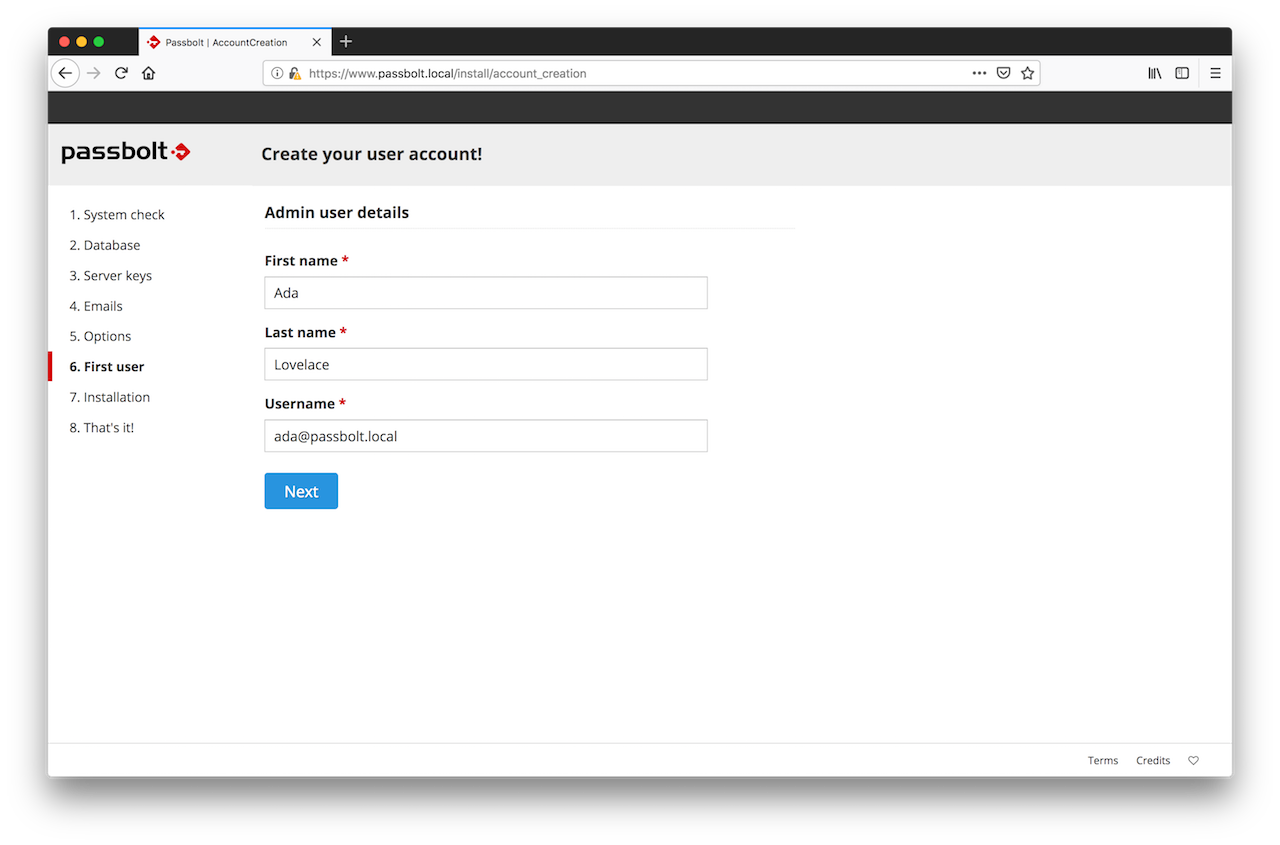
2.6. First User Creation
You need to create the first admin user account. This first admin user is probably you, so enter your details and click on next.
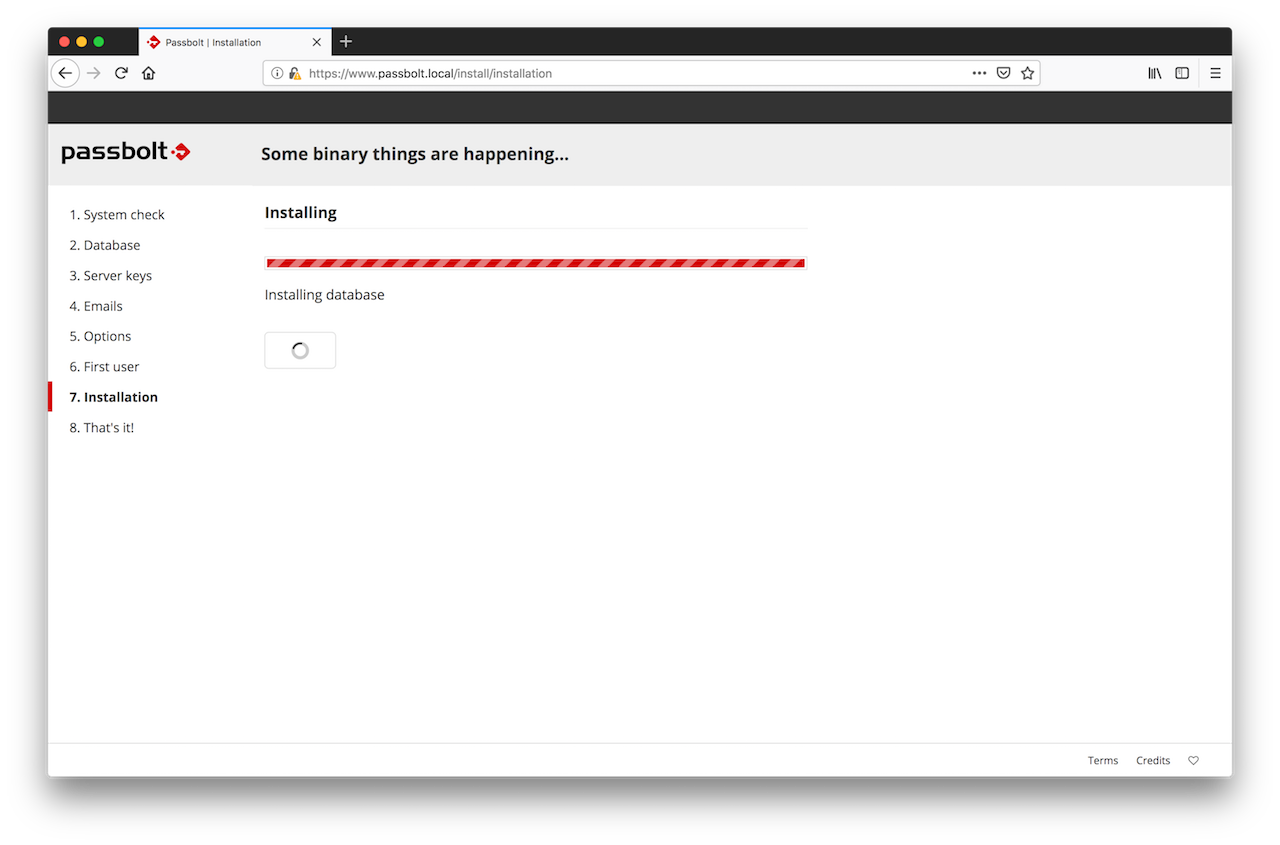
2.7. Installation
That's it. The wizard has now enough information to proceed with the configuration of passbolt. Sit back and relax for a few seconds while the configuration process is going on.
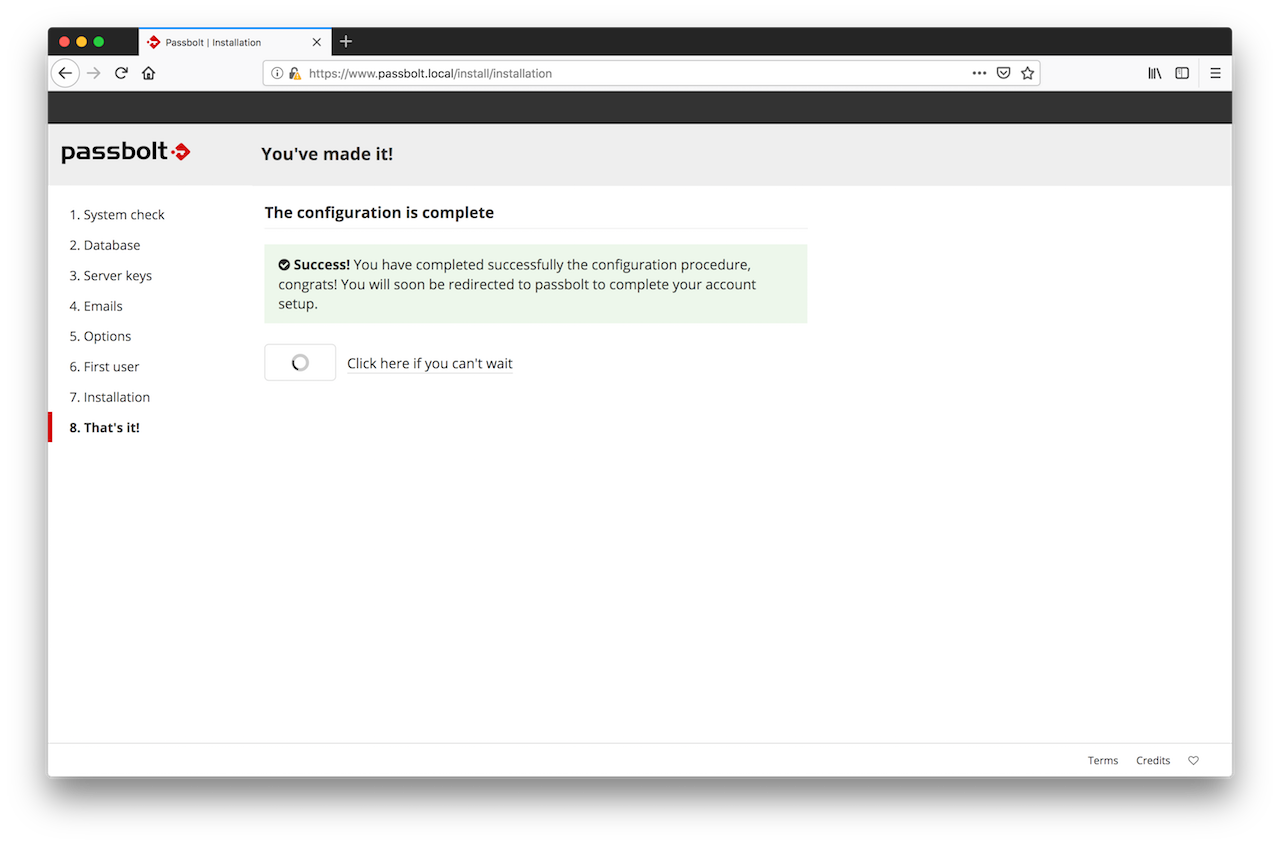
Your user account is now created. You will see a redirection page for a few second and then will be redirected to the user setup process so that you can configure your user account.
2.8. HTTPS setup process
Depending on your needs there are two different options to setup nginx and SSL using the package:
3. Configure your administrator account
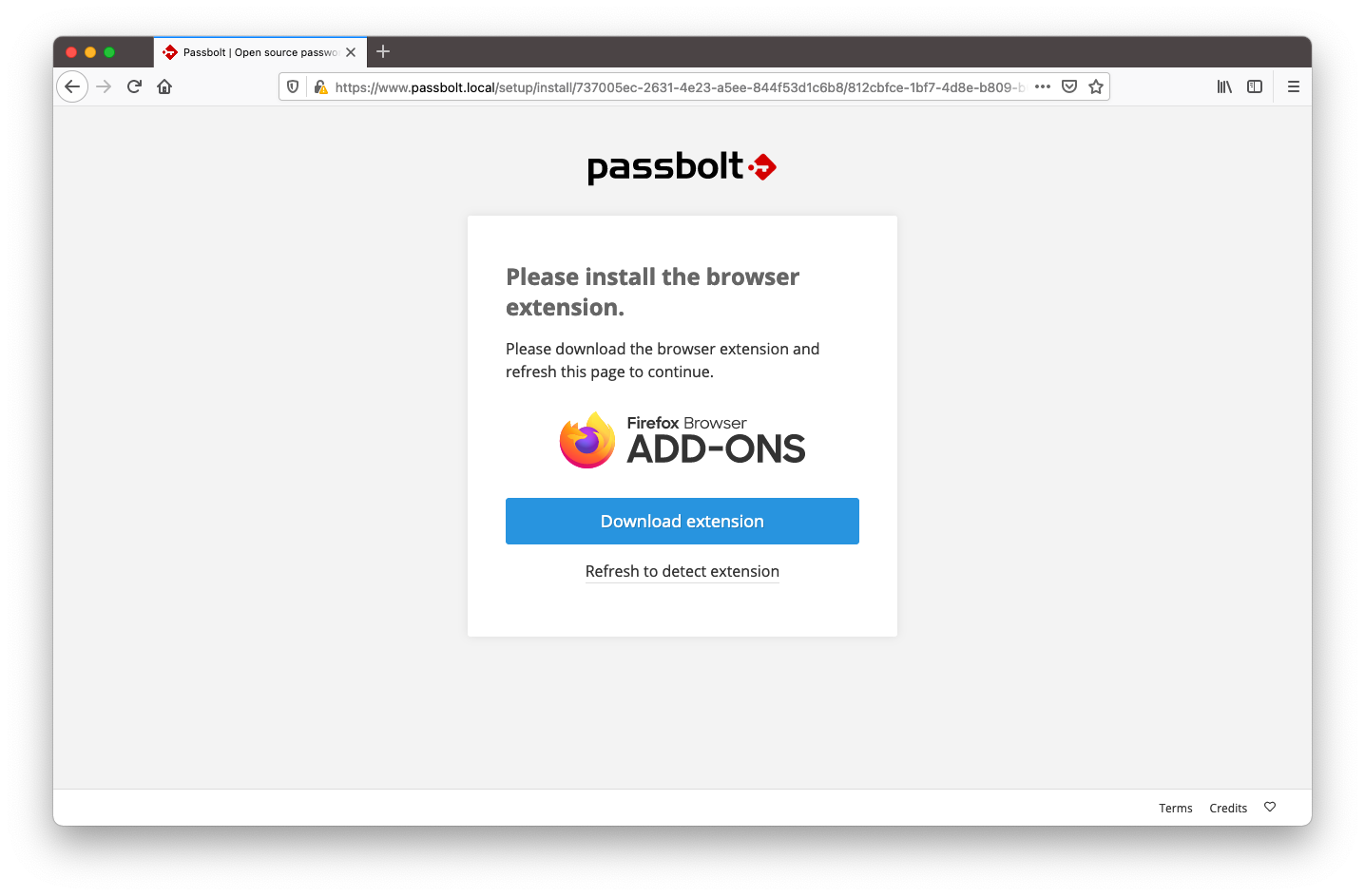
3.1. Download the plugin
Before continuing passbolt will require you to download its plugin. If you already have it installed you can go to the next step.
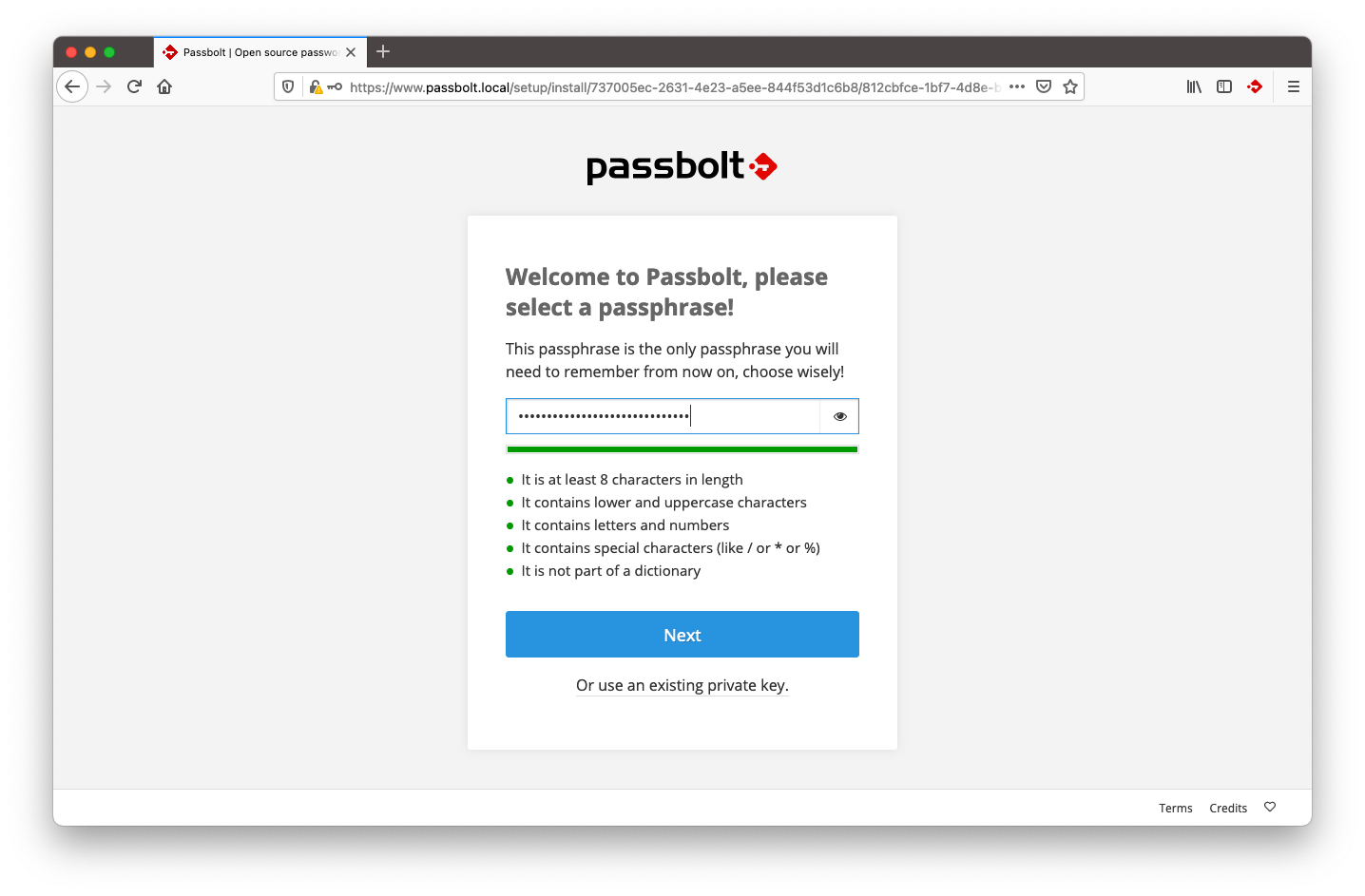
3.2. Create a new key
Passbolt will ask you to create or import a key that will be later use to identify you and encrypt your passwords. Your key needs to be protected by a password. Choose it wisely, it will be the gatekeeper to all your other passwords.
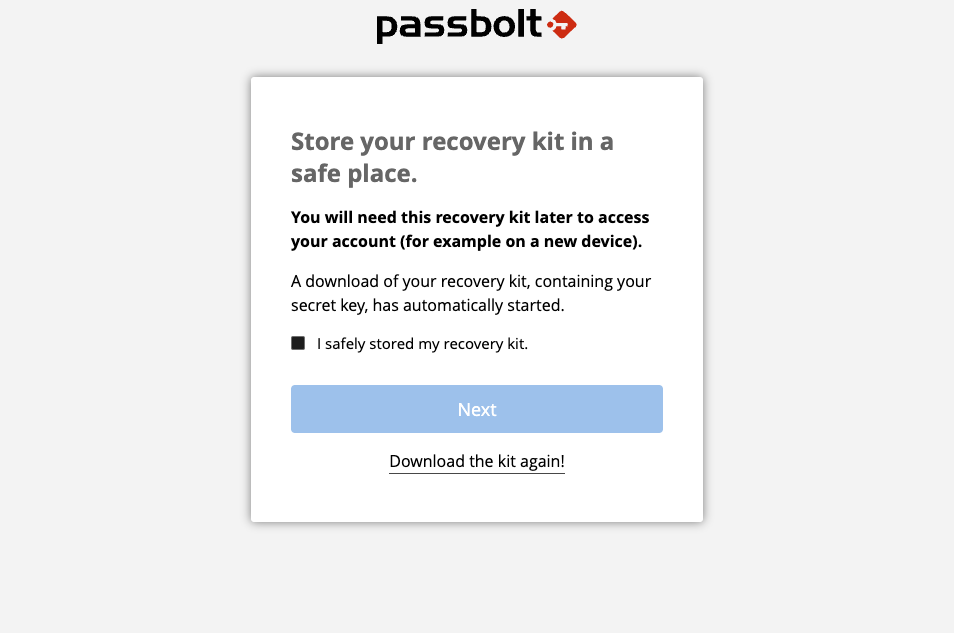
3.3. Download your recovery kit
This step is essential. Your key is the only way to access your account and passwords. If you lose this key (by breaking or losing your computer and not having a backup for example), your encrypted data will be lost even if you remember your passphrase.
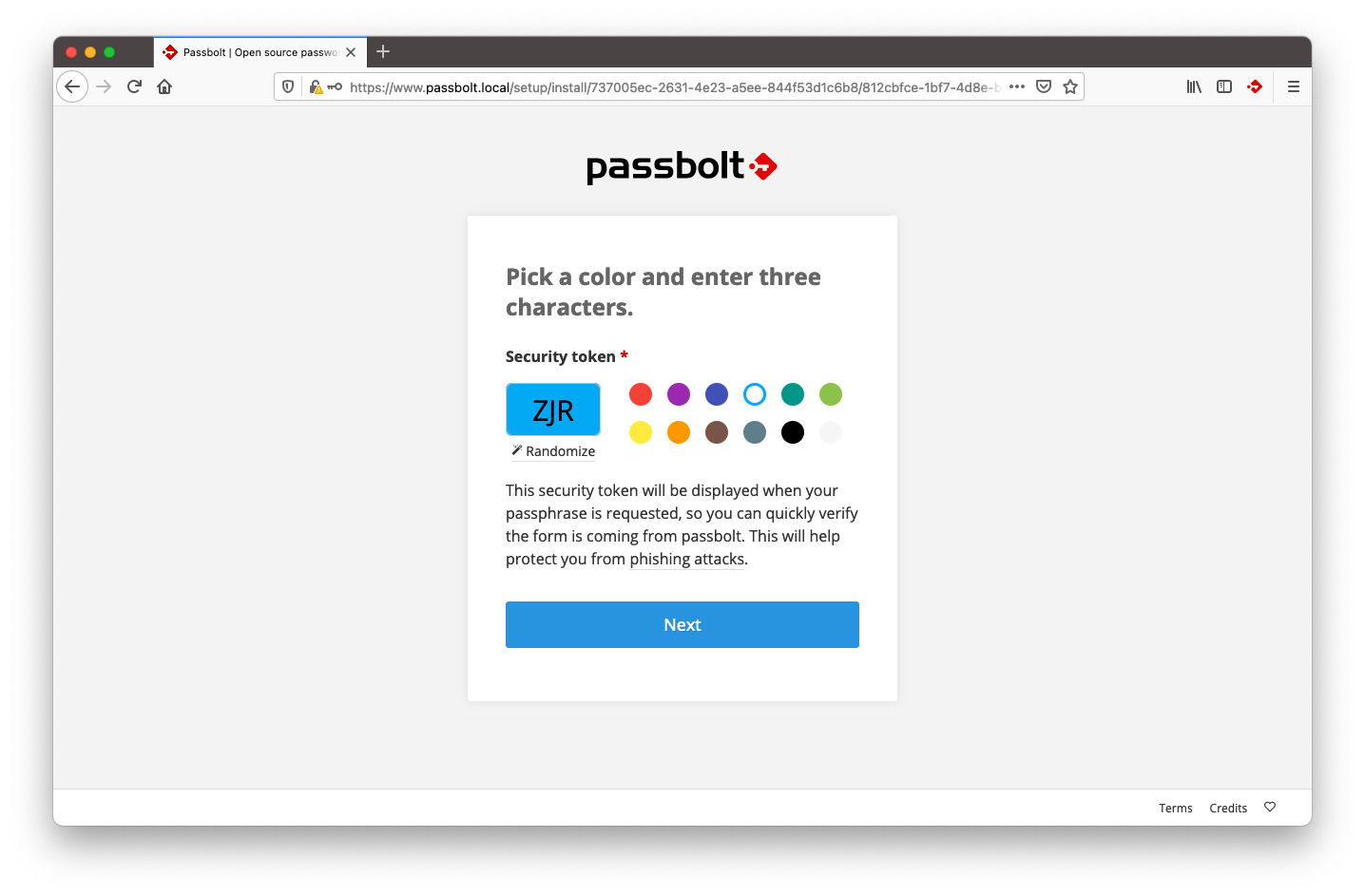
3.4. Define your security token
Choosing a color and a three characters token is a secondary security mechanism that helps you to mitigate phishing attacks. Each time you are performing a sensitive operation on passbolt, you should see this token.
3.5. That's it!
Your administrator account is configured. You will be redirected to the login page of passbolt. Enjoy!